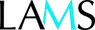<Method Name="MQ-LDAP" Enabled="true">
<Param Name="java.naming.factory.initial">com.sun.jndi.ldap.LdapCtxFactory</Param>
<Param Name="java.naming.provider.url">ldap://192.168.111.35</Param>
<Param Name="java.naming.security.authentication">simple</Param>
<Param Name="principalDNPrefix">cn=</Param>
<Param Name="principalDNSuffix">,dc=melcoe,dc=local</Param>
<Param Name="dsJndiName">java:/jdbc/lams-ds</Param>
<Param Name="principalsQuery">select password from lams_user where login=?</Param>
<Param Name="rolesQuery">
SELECT DISTINCT r.name,'Roles' FROM
lams_user u LEFT OUTER JOIN lams_user_organisation uo USING(user_id)
LEFT OUTER JOIN lams_user_organisation_role urr USING(user_organisation_id)
LEFT OUTER JOIN lams_role r USING (role_id)
WHERE u.login=?
</Param>
<!--
Uncomment the following if connecting using SSL
<Param Name="java.naming.security.protocol">ssl</Param>
<Param Name="truststore.path">D:/MQLdapTrustStore</Param>
<Param Name="truststore.password">webauth</Param>
-->
</Method>
This is from the original lamsauthentication.xml, as I don't have a copy of 2.0.3 working with ldap - but that's essentially what it should look like (with your settings for the provider url, and principal prefix/suffix).
If you haven't already, have a look at the wiki page at http://wiki.lamsfoundation.org/display/lams/LDAP, there are two things to consider when using LDAP in 2.0.3. Firstly the passwords sent by LAMS to LDAP are already encrypted - so LDAP can't be expecting a cleartext password. Secondly users have to be created manually on the LAMS side, and then flagged in the database to authenticate with LDAP.
Posted by Jun-Dir Liew